
Ex-Conti ransomware members have actually coordinated with the FIN7 risk stars to disperse a brand-new malware household called ‘Domino’ in attacks on business networks.
Domino is a reasonably brand-new malware household including 2 parts, a backdoor called ‘Domino Backdoor,’ which in turn drops a ‘Domino Loader’ that injects an info-stealing malware DLL into the memory of another procedure.
IBM’s Security Intelligence scientists have actually been tracking ex-Conti and TrickBot members making use of the brand-new malware in attacks because February 2023.
Nevertheless, a brand-new IBM report launched Friday connects the real advancement of the Domino malware to the FIN7 hacking group– a cybercriminal attire connected to a range of malware, and the BlackBasta and DarkSide ransomware operations.
The Domino Malware attacks
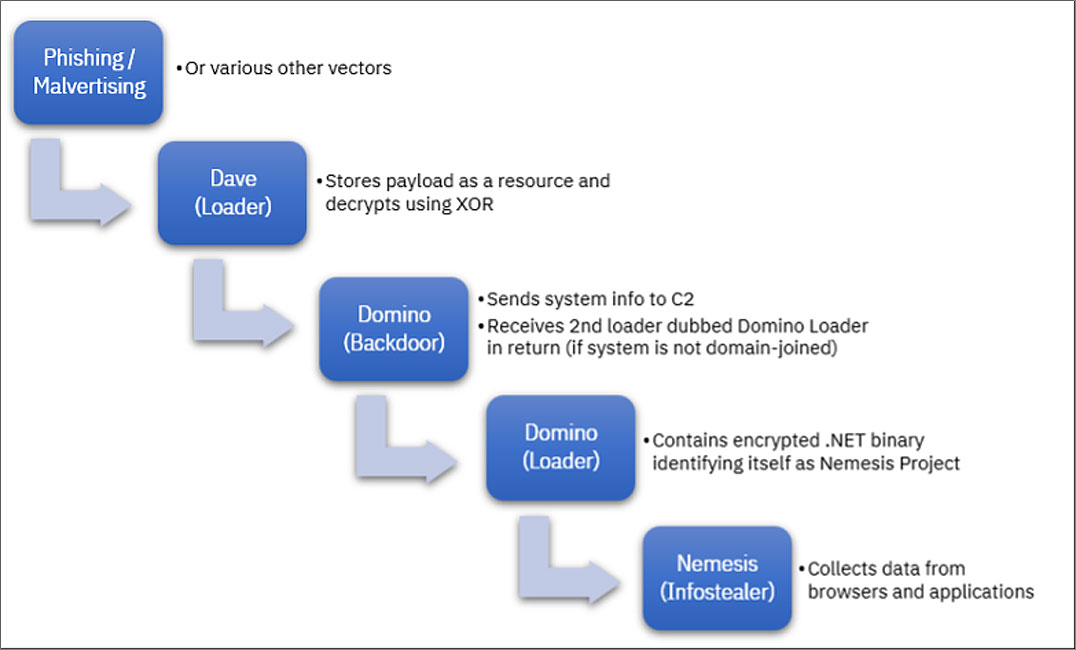
Because the fall of 2022, IBM scientists have actually been tracking attacks utilizing a malware loader called ‘Dave Loader’ that is connected to previous Conti ransomware and TrickBot members.
This loader was seen releasing Cobalt Strike beacons that make use of a ‘206546002’ watermark, observed in attacks from by ex-Conti members in the Royal and Play ransomware operations
IBM states Dave Loader has actually likewise been seen releasing Emotet, which was utilized nearly specifically by the Conti ransomware operation in June 2022, and after that later on by the BlackBasta and Quantum ransomware gangs.
Nevertheless, more just recently, IBM states they have actually seen Dave Loader setting up the brand-new Domino malware household.
A lot of typically, Dave Loader would drop ‘Domino Backdoor,’ which would then set up ‘Domino Loader.’
Domino Backdoor is a 64-bit DLL that will mention system info, such as running procedures, usernames, computer system names, and send it back to the aggressor’s Command and Control server. The backdoor likewise gets commands to carry out or additional payloads to set up.
The backdoor was seen downloading an extra loader, Domino Loader, that sets up an embedded.NET info-stealer called ‘Bane Task.’ It can likewise plant a Cobalt Strike beacon, for higher determination.
” The Domino Backdoor is created to call a various C2 address for domain-joined systems, recommending a more capable backdoor, such as Cobalt Strike, will be downloaded on greater worth targets rather of Task Bane,” describes the IBM scientists Charlotte Hammond and Ole Villadsen.
Source: IBM
Task Bane is a basic information-stealing malware that can gather qualifications saved in internet browsers and applications, cryptocurrency wallets, and internet browser history.
Ex-Conti members coordinate with FIN7
Danger stars, particularly those who make use of ransomware, typically partner with other risk groups to disperse malware and for preliminary access to business networks.
For instance, TrickBot, Emotet, BazarBackdoor, and QBot (QakBot) have a long history of offering preliminary access to ransomware operations, such as REvil, Labyrinth, Egregor, BlackBasta, Ryuk, and Conti.
In time, the lines in between the malware designers and the ransomware gangs have actually grown dirty, making comparing the 2 operations hard.
With the development of the Conti cybercrime distribute, these lines faded a lot more as the ransomware operation presumed control of both TrickBot and BazarBackdoor’s advancement for their own operations.
In Addition, after Conti closed down, the ransomware operation splintered into smaller sized cells, with members moving all over the ransomware area, consisting of Royal, Play, Quantum/Zeon/Dagon, BlackBasta, LockBit, and more.
IBM has actually associated the Domino malware household to FIN7 due to a good deal of code overlap with Lizar (aka Tirion and DiceLoader), a post-exploitation toolkit related to FIN7.
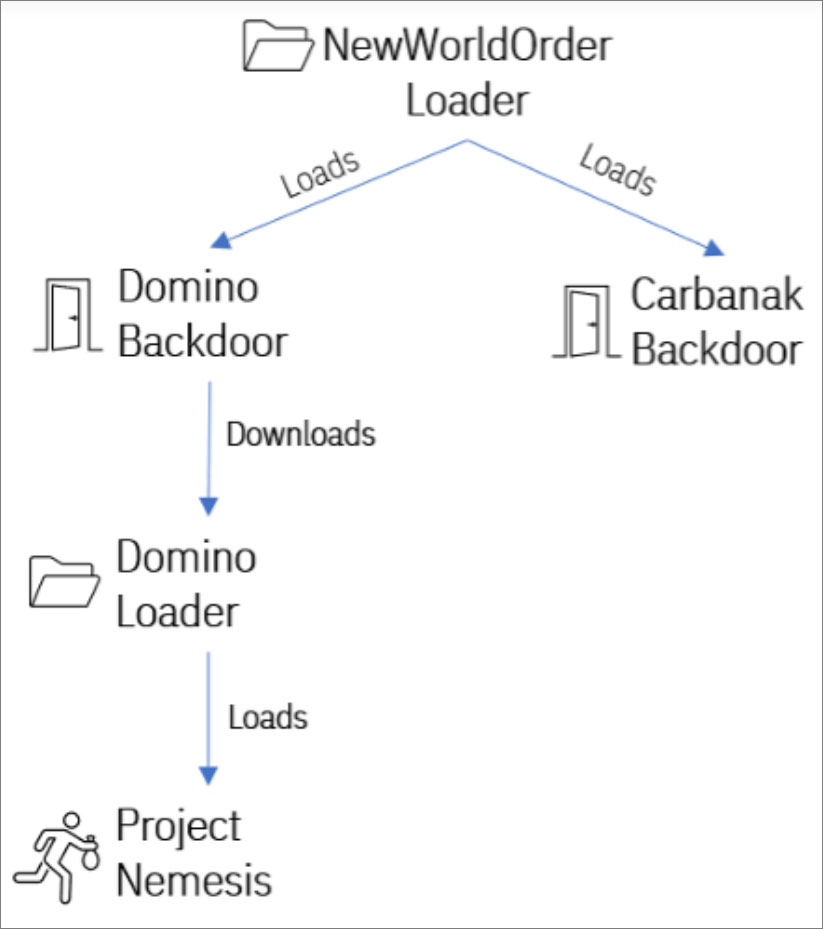
Moreover, IBM discovered that a loader called ‘NewWorldOrder,’ generally utilized in FIN7’s Carbanak attacks, was just recently utilized to press the Domino malware.
Source: IBM
So, in a complicated joint endeavor, we have Dave Loader (TrickBot/Conti) pressing the Domino (FIN7) malware, which in turn releases Task Bane or Cobalt Strike beacons thought to be related to ex-Conti member ransomware activity.
This indicates that protectors need to handle a complicated web of risk stars, all with malware enabling remote access to networks.